The allure of having applications and systems hosted on a cloud network is appealing to community banks and credit unions as it allows them to eliminate servers, internal infrastructure, and applications that would typically have to be hosted inside the institution, as well as the associated support each one requires. As a result, many organizations are considering, or currently in the process of, moving to cloud-based systems.
While the cloud can certainly help streamline processes and increase bandwidth for bank staff, there are a number of details that community banks and credit unions should consider before making this transition, beginning with the cloud destinations or management types:
The Infrastructure Management Types
All hardware is located on-site at the financial institution.
All hardware is housed at a third-party data center. This solves the issue of location.
A cloud provider hosts the infrastructure components traditionally housed in an on premise data center, including servers, storage and networking hardware. It solves the issue of location + hardware storage.
A cloud computing model where a third-party provider delivers hardware and software tools to users over the internet. This model solves the issues of location + hardware + platform.
A software distribution model in which a third-party provider hosts applications and makes them available to customers over the Internet. Some examples include Gmail, Facebook and Office365. This model solves the issues of location + hardware + platform + software.
Cloud services offer many benefits for financial institutions, including system standardization, centralization of information, the simplification of IT management and the built-in ability to stay current with technology updates and vendor software releases. For cloud services to be implemented successfully, financial institutions must understand the different types of cloud environments that are available and which one best meets the strategic objectives of their institution. Each bank has a unique corporate strategy that will guide how it moves to the cloud, what type of cloud solution is best for its environment and what specific technology assets should be moved to the cloud.
Here are five questions you should ask before making the decision to move to the cloud:
- Which applications can we move to the cloud?
Evaluating which applications can be moved to the cloud and which vendors offer cloud-based solutions is really the first step. This will help organizations understand issues and elements that will be solved or created by the move to the cloud. For example, even with cloud-based solutions, financial institutions will still need to manage user work stations, security issues, connections to applications, and switches and routers, to name a few.
- Does moving to the cloud fit with our corporate strategy?
Some organizations consider moving to the cloud simply because they think it is the right thing to do; however, there is no set path that all financial institutions must follow. Each bank has a unique strategy that is driven by its market situation, such as the desire to expand service offerings, open new branches, merge with another institution or even be acquired. Your corporate strategy informs your institution’s IT strategy and will guide you in choosing the management type that best fits your overall goal.
- Is the connectivity at my bank strong enough to support cloud-based solutions?
Delays in loading cloud-based applications can be frustrating as well as costly. The increased use of cloud-based computing will place added demands on Internet speed and connectivity, making a strong connection critical for the success and health of the financial institution. This is a very important consideration when determining whether to move to cloud-based services. Confirming your institution has the proper connectivity will certainly help streamline this transition.
- Are there additional security, risk and compliance issues to consider when moving to the cloud?
Moving to a cloud-based application will mean giving up some controls to the cloud vendor. When selecting a cloud vendor, evaluate their practices and strategies for user identity and access management, data protection, incident response and SOC 2 Type II documentation. You should have a solid vendor management program in place to verify that your vendors are compliant and are following the service agreement.
- Will moving to the cloud save my institution money and cut down on IT costs?
Many financial institutions find that the transition does not translate to a lower price tag, and in-fact can result in the bank actually spending more. However, with this expense comes the simplification of IT management and the built-in ability to stay up to date with software releases. Migrating to the cloud commonly requires an organization to move from a capital expenditure (CAPEX) to an operating expenditure (OPEX) financial model, in which large capital outlays for purchase of servers, computers and networking hardware, are replaced by monthly, quarterly, or annual fees that an institution pays to operate the application.
An application hosted in the cloud does not require any major capital investments for the institution. While the monthly fee in the OPEX model may be higher than the hardware and software costs, it eliminates the responsibility and indirect expense of bank personnel having to maintain the IT infrastructure. Think of these pricing models in the same way as owning a car versus taking Uber. When you own a car, you are responsible for its general upkeep, paying for gas, cleaning the car, etc. When you take Uber you simply pay for the ride and the driver is responsible for the vehicle’s upkeep. While you may pay a little more for that Uber ride, you gain more free time to focus on activities you enjoy.
Working with a financial industry IT service provider, like Safe Systems, can help you with the decision-making process involved with moving to the cloud while ensuring the solution and applications are compliant and meet regulatory expectations. We work with each institution to create a plan, based on their goals and strategies, to determine what can and should be moved to the cloud. Ultimately, moving IT assets to the cloud enables your bank and IT executives to focus on the key capabilities that support your bank’s unique strategy.















 Be sure that all products your vendors are “sun setting” are budgeted to be updated or replaced. Also, ensure that key applications and settings are updated to the latest best practices, including:
Be sure that all products your vendors are “sun setting” are budgeted to be updated or replaced. Also, ensure that key applications and settings are updated to the latest best practices, including:









 Each new regulatory guidance, update, change, and interpretation requires additional expertise and more employee resources. It’s a never ending cycle. The last decade has brought about an increase in compliance changes including: the
Each new regulatory guidance, update, change, and interpretation requires additional expertise and more employee resources. It’s a never ending cycle. The last decade has brought about an increase in compliance changes including: the 






 The bank sought a trusted technology partner that clearly understood IT and compliance processes for financial institutions and had the expertise to monitor and manage the network efficiently. The bank’s new CEO had previous experience working with Safe Systems while at another bank and recommended they contact the outsourced IT provider. The bank chose to partner with Safe Systems and utilize its NetComply® One IT network management solution.
The bank sought a trusted technology partner that clearly understood IT and compliance processes for financial institutions and had the expertise to monitor and manage the network efficiently. The bank’s new CEO had previous experience working with Safe Systems while at another bank and recommended they contact the outsourced IT provider. The bank chose to partner with Safe Systems and utilize its NetComply® One IT network management solution. 



 A relatively new term, RegTech, refers to a set of companies and solutions that address regulatory challenges through innovative technology. RegTech is a subset of FinTech that focuses on technologies that facilitate the delivery of regulatory requirements more efficiently and effectively than traditional compliance processes.
A relatively new term, RegTech, refers to a set of companies and solutions that address regulatory challenges through innovative technology. RegTech is a subset of FinTech that focuses on technologies that facilitate the delivery of regulatory requirements more efficiently and effectively than traditional compliance processes.  Due to the complexity and momentum of regulatory changes, RegTech solutions must be customizable and easy to integrate into a variety of environments. No two institutions are alike but properly designed RegTech solutions should help to guide institutions to a better overall compliance posture.
Due to the complexity and momentum of regulatory changes, RegTech solutions must be customizable and easy to integrate into a variety of environments. No two institutions are alike but properly designed RegTech solutions should help to guide institutions to a better overall compliance posture. 

 While it is true that outsourcing can be expensive, the benefits have proven to consistently
While it is true that outsourcing can be expensive, the benefits have proven to consistently  It is simply no longer necessary for IT partners to be onsite to
It is simply no longer necessary for IT partners to be onsite to  Regardless of location and size, small community banks and credit unions are under most of the same regulations as larger institutions, forcing a small IT staff to be well-versed in all regulatory guidance from cybersecurity to disaster recovery to meet examiner expectations. Auditors and examiners expect thorough documentation to prove that the institution’s daily practices match its defined policies and procedures. Financial institutions should not wait for a negative review finding to take a proactive approach to network management. Working with service providers that have dedicated staff and experts who understand the financial industry’s regulatory requirements and best practices ensures the required planning and reporting is completed in a timely manner.
Regardless of location and size, small community banks and credit unions are under most of the same regulations as larger institutions, forcing a small IT staff to be well-versed in all regulatory guidance from cybersecurity to disaster recovery to meet examiner expectations. Auditors and examiners expect thorough documentation to prove that the institution’s daily practices match its defined policies and procedures. Financial institutions should not wait for a negative review finding to take a proactive approach to network management. Working with service providers that have dedicated staff and experts who understand the financial industry’s regulatory requirements and best practices ensures the required planning and reporting is completed in a timely manner.  There are hundreds of tasks that a small IT staff must complete on a regular basis to keep the bank’s operations running efficiently. Many community financial institutions have limited in-house resources dedicated to IT network functions. If a critical staff member goes on a
There are hundreds of tasks that a small IT staff must complete on a regular basis to keep the bank’s operations running efficiently. Many community financial institutions have limited in-house resources dedicated to IT network functions. If a critical staff member goes on a  Without a doubt, the core banking platform is central to all financial institutions. However, you may be taking unnecessary risk by relying on them for all your needs. An IT services provider can help alleviate the stress by evaluating the infrastructure of the bank without bias, and eliminating the unnecessary hardware, processes and tasks, helping with overall management and ongoing cost. Whether it be network management, security, or compliance, it is unlikely your core will match the expertise a specialized partner can offer. Network management providers offer unbiased advice, while also diversifying your risk.
Without a doubt, the core banking platform is central to all financial institutions. However, you may be taking unnecessary risk by relying on them for all your needs. An IT services provider can help alleviate the stress by evaluating the infrastructure of the bank without bias, and eliminating the unnecessary hardware, processes and tasks, helping with overall management and ongoing cost. Whether it be network management, security, or compliance, it is unlikely your core will match the expertise a specialized partner can offer. Network management providers offer unbiased advice, while also diversifying your risk. Many financial institutions struggle with choosing the right solutions partner. Smaller institutions in particular can benefit from outsourcing or partnering with a provider who offers network management solutions exclusively tailored for community banks and credit unions. Having a system in place that offers key features such as patch management, third party patching, antivirus, hardware and software inventory management, vulnerability remediation, and compliance-focused reporting to verify that your financial institution’s network is adhering to your policies and procedures is critical in today’s environment.
Many financial institutions struggle with choosing the right solutions partner. Smaller institutions in particular can benefit from outsourcing or partnering with a provider who offers network management solutions exclusively tailored for community banks and credit unions. Having a system in place that offers key features such as patch management, third party patching, antivirus, hardware and software inventory management, vulnerability remediation, and compliance-focused reporting to verify that your financial institution’s network is adhering to your policies and procedures is critical in today’s environment.











 Aside from having a BCP and associated
Aside from having a BCP and associated 
 Typically, a regulatory agency will not revisit the findings again until the next review. It is up to the financial institution to address each point and provide the proper documentation to show these items have been corrected before the next meeting. For example, if the bank’s antivirus was listed as out of date on the findings report, the institution would have to update each machine, run a report, and include this information in the findings package to be reviewed by the regulatory agency during the next visit. To complete the process efficiently, banks must keep up with who is in charge of each specific action item, when the item is due for completion, and which reports should be included in the findings package.
Typically, a regulatory agency will not revisit the findings again until the next review. It is up to the financial institution to address each point and provide the proper documentation to show these items have been corrected before the next meeting. For example, if the bank’s antivirus was listed as out of date on the findings report, the institution would have to update each machine, run a report, and include this information in the findings package to be reviewed by the regulatory agency during the next visit. To complete the process efficiently, banks must keep up with who is in charge of each specific action item, when the item is due for completion, and which reports should be included in the findings package.




 Often there is one person in charge of the review and they must work with each department to gather information by the designated due date. All files must then be stored in a central location, follow the template the reviewing agents have requested and be in a format that can be transmitted securely to the requesting party. Gathering all this information and ensuring all documents are complete and accurate can be a challenging task for smaller community banks and credit unions with limited in-house resources and staff.
Often there is one person in charge of the review and they must work with each department to gather information by the designated due date. All files must then be stored in a central location, follow the template the reviewing agents have requested and be in a format that can be transmitted securely to the requesting party. Gathering all this information and ensuring all documents are complete and accurate can be a challenging task for smaller community banks and credit unions with limited in-house resources and staff.



 Many financial institutions are turning to IT and security service providers to act as an extension of their organization and help augment internal technology and compliance resources. The right third-party solution provider can serve as a true partner and work alongside current staff to manage the technology, compliance and regulatory aspects of the institution. When the technology or compliance staff is out or unavailable, outsourcing select business processes helps fill the personnel gap and provide added stability for the institution and peace of mind to all.
Many financial institutions are turning to IT and security service providers to act as an extension of their organization and help augment internal technology and compliance resources. The right third-party solution provider can serve as a true partner and work alongside current staff to manage the technology, compliance and regulatory aspects of the institution. When the technology or compliance staff is out or unavailable, outsourcing select business processes helps fill the personnel gap and provide added stability for the institution and peace of mind to all.





 This was the case for Pembroke, N.C.-based Lumbee Guaranty Bank. To ensure his institution maintained compliance, Austin Maynor, Information Security Officer at Lumbee Guaranty Bank, manually filled out the CAT with the help of a spreadsheet, but quickly found this process to be an extremely time-consuming project to complete. He determined the bank needed a solution that could give them a better understanding of where they were in terms of cybersecurity preparedness and where they needed to be in order to maintain compliance.
This was the case for Pembroke, N.C.-based Lumbee Guaranty Bank. To ensure his institution maintained compliance, Austin Maynor, Information Security Officer at Lumbee Guaranty Bank, manually filled out the CAT with the help of a spreadsheet, but quickly found this process to be an extremely time-consuming project to complete. He determined the bank needed a solution that could give them a better understanding of where they were in terms of cybersecurity preparedness and where they needed to be in order to maintain compliance.



 The CAT also enables financial institutions to review their Inherent Risk Profile in relation to their Cybersecurity Maturity results, which will indicate if they are aligned. As one might expect, as inherent risk rises, an institution’s maturity level should also increase. However, an institution’s inherent risk profile and maturity levels will change over time as threats, vulnerabilities, and operational environments change, making it necessary for institutions to complete the CAT periodically or when making adjustments to their organizations.
The CAT also enables financial institutions to review their Inherent Risk Profile in relation to their Cybersecurity Maturity results, which will indicate if they are aligned. As one might expect, as inherent risk rises, an institution’s maturity level should also increase. However, an institution’s inherent risk profile and maturity levels will change over time as threats, vulnerabilities, and operational environments change, making it necessary for institutions to complete the CAT periodically or when making adjustments to their organizations. 

 Even though the CAT is voluntary, all financial institutions are required to evaluate inherent risk and cybersecurity maturity in some way, which requires a robust assessment program. Completing the CAT is a good way to prepare for audits since the guidelines provide community banks and credit unions with detailed information on the federal government’s expectations for cybersecurity preparedness. The CAT enables financial institutions to identify vulnerabilities, fill in security gaps, and demonstrate a stronger security posture before the examination begins.
Even though the CAT is voluntary, all financial institutions are required to evaluate inherent risk and cybersecurity maturity in some way, which requires a robust assessment program. Completing the CAT is a good way to prepare for audits since the guidelines provide community banks and credit unions with detailed information on the federal government’s expectations for cybersecurity preparedness. The CAT enables financial institutions to identify vulnerabilities, fill in security gaps, and demonstrate a stronger security posture before the examination begins. 
 One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.
One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.

 Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible.
Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible. 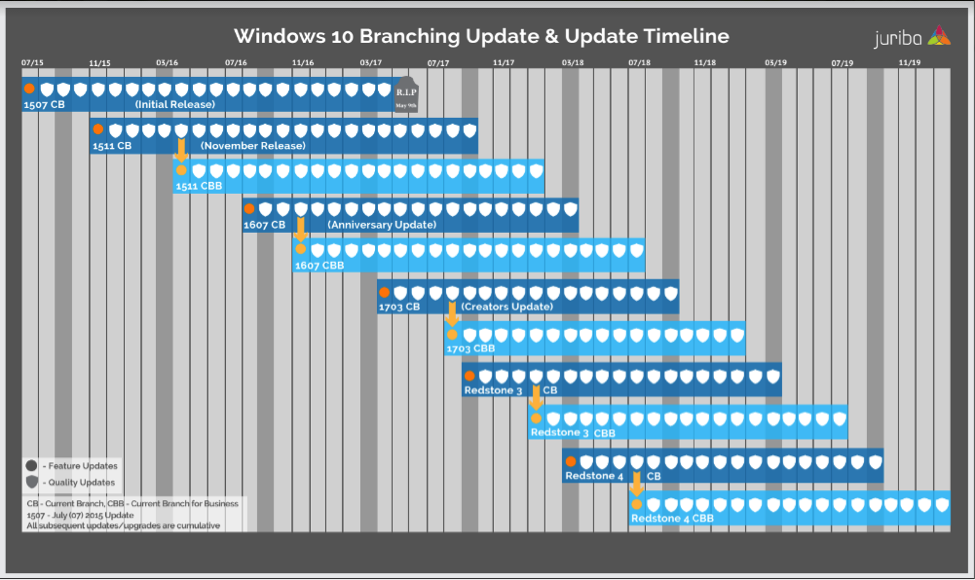






 Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations.
Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations. 



 Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank.
Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank. 



 To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.
To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.



 This guidance is always changing, and financial institutions must adapt to regulatory demands. IT auditors and examiners will look for evidence of a thorough risk assessment; make sure that written policies and procedures align with the assessment; and then verify that controls and daily practices are appropriate.
This guidance is always changing, and financial institutions must adapt to regulatory demands. IT auditors and examiners will look for evidence of a thorough risk assessment; make sure that written policies and procedures align with the assessment; and then verify that controls and daily practices are appropriate.









 Oconee State Bank had already successfully implemented a previous version of Safe Systems’
Oconee State Bank had already successfully implemented a previous version of Safe Systems’ 
 Safe Systems currently monitors more than 20,000 devices and roughly 80% of all issues addressed come through our monitoring systems. Just by implementing Safe Systems NetComply One with SSAI, the number of alerts sent to an IT support team is decreased by an average of 89%. By effectively correcting known problems and only notifying your team about more significant issues, SSAI creates tremendous value for your institution, your employees and your infrastructure.
Safe Systems currently monitors more than 20,000 devices and roughly 80% of all issues addressed come through our monitoring systems. Just by implementing Safe Systems NetComply One with SSAI, the number of alerts sent to an IT support team is decreased by an average of 89%. By effectively correcting known problems and only notifying your team about more significant issues, SSAI creates tremendous value for your institution, your employees and your infrastructure.
 Regulations define cybersecurity as:
Regulations define cybersecurity as: Regulators expect financial institutions to be not just cyber-secure, but cyber resilient, and that requires close cooperation with all their critical third-parties. Assessing and managing risks, and developing capabilities for response and recovery in the event of disruptions regardless of where they may occur, requires financial institutions to have proven plans in place to meet regulatory expectations. The FFIEC has issued specific guidance on how it expects organizations to manage this process. The FFIEC IT Examination Handbook’s “
Regulators expect financial institutions to be not just cyber-secure, but cyber resilient, and that requires close cooperation with all their critical third-parties. Assessing and managing risks, and developing capabilities for response and recovery in the event of disruptions regardless of where they may occur, requires financial institutions to have proven plans in place to meet regulatory expectations. The FFIEC has issued specific guidance on how it expects organizations to manage this process. The FFIEC IT Examination Handbook’s “








 In today’s banking environment, community banks recognize and embrace the use of technology and remain committed to investing in new technologies and services moving forward. In fact, nearly 77% of respondents claim they are spending more on technology today than they have in the past. However, the challenge often lies in trying to keep pace with the rapid rate of change that is influencing their business. Community banks are continuing to explore ways to enhance and augment their IT departments, as many institutions struggle to maintain adequate personnel needed to manage the complex activities required of the IT department. To counter this, 71% of respondents have turned to outsourcing their network management and 63% have outsourced their IT support.
In today’s banking environment, community banks recognize and embrace the use of technology and remain committed to investing in new technologies and services moving forward. In fact, nearly 77% of respondents claim they are spending more on technology today than they have in the past. However, the challenge often lies in trying to keep pace with the rapid rate of change that is influencing their business. Community banks are continuing to explore ways to enhance and augment their IT departments, as many institutions struggle to maintain adequate personnel needed to manage the complex activities required of the IT department. To counter this, 71% of respondents have turned to outsourcing their network management and 63% have outsourced their IT support.

 Banks should make continual service improvement a key part of their overall corporate culture. These changes can be identified by a single resource or through a committee focusing on operational improvement. Allocating time and resources to focus on the right aspects of new technology and process improvement is key as even the smallest incremental changes can have the ability to provide a significant positive impact.
Banks should make continual service improvement a key part of their overall corporate culture. These changes can be identified by a single resource or through a committee focusing on operational improvement. Allocating time and resources to focus on the right aspects of new technology and process improvement is key as even the smallest incremental changes can have the ability to provide a significant positive impact. 

 It is important to make sure that all functional areas of the institution are involved in testing. This means that in addition to the Senior Management and Information Security roles defined in your plan, the team should also consist of key department heads with detailed operating knowledge of the processes and functions impacted by your scenario. These individuals must be aware of how to quickly recover and adequately support customer needs, regardless of whether normal operating procedures are available. Therefore, tests should cover the steps departmental managers must take to complete functions manually or in an alternate way. Although technology is important, the disaster response must not hinge on waiting for technology glitches to be resolved. Your departmental specialists know how to do their job under normal circumstances, but including them in testing allows them to gain familiarity with their alternate procedures in a specific emergency scenario.
It is important to make sure that all functional areas of the institution are involved in testing. This means that in addition to the Senior Management and Information Security roles defined in your plan, the team should also consist of key department heads with detailed operating knowledge of the processes and functions impacted by your scenario. These individuals must be aware of how to quickly recover and adequately support customer needs, regardless of whether normal operating procedures are available. Therefore, tests should cover the steps departmental managers must take to complete functions manually or in an alternate way. Although technology is important, the disaster response must not hinge on waiting for technology glitches to be resolved. Your departmental specialists know how to do their job under normal circumstances, but including them in testing allows them to gain familiarity with their alternate procedures in a specific emergency scenario.