In today’s technological landscape, where every computing resource is online and susceptible to attack and malicious activity, server hardening is an important process for financial institutions to have in place. Every day servers are targeted by harmful malware, ransomware, and other malicious attacks.
The best defense against these threats is to ensure that server hardening is a well-established practice within your community bank or credit union. Server hardening is the process of enhancing server security through a variety of means, which results in a more secure server operating environment due to the advanced security measures that are put in place during the hardening process.
 One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.
One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.
To help streamline this time-consuming but essential process, Safe Systems designed its unique Security Baseline Service to work with its NetComply® One IT network management service to help automate the server hardening process. The Security Baseline Service leverages aggregate vulnerability scan data and remediates vulnerabilities across the service’s customer base. The service implementation includes a testing phase and ticketing notification to alert the institution of remediated vulnerabilities to help alleviate attacks and ensure networks are secure and up to date.
The Security Baseline process includes:
- Remediation of emerging security vulnerabilities
- Vulnerabilities identified by Safe Systems’ and its partners, which includes:
- Evaluating commonly found vulnerabilities on a monthly basis
- Determining significance of vulnerabilities
- Writing remediation procedures for significant commonly found vulnerabilities
- Monthly remediation across all subscribed devices
- Ticket generated detailing remediation application results
- Comprehensive report detailing individual fixes
- Remediation of vulnerabilities outside our sampling group available upon request at an hourly rate
Many of the vulnerability findings banks receive are often related to software issues that are addressed by updates or patches that pass Safe Systems’ testing procedure and then seamlessly executed on a daily basis. To ensure compliance, these patches and processes are implemented based on the FFIEC’s patch management guidelines outlined in the 2016 Information Security Booklet.
Financial institutions utilizing Security Baseline also benefit from the prolonged testing period Safe Systems uses to verify that Service Packs and new Windows builds will work with existing software. This ensures updates will be supported by the networks and any new features introduced will not cause problems for the institutions. The extra level of testing helps banks and credit unions avoid unnecessary IT challenges and network issues, reducing downtime and freeing up IT staff to focus on more pressing activities.
At Safe Systems, our goal is to reduce the amount of time internal IT staff must spend on time consuming activities such as examining vulnerability assessment reports, troubleshooting services and patch management issues. We are constantly working to create automation to provide the best experience to our customers and ensure all networks are secure and in compliance with government regulations.
7 Reasons Why Small Community Banks Should Outsource IT Network Management
This is a free white paper that addresses key issues smaller financial institutions face when managing their networks and the benefits of outsourcing these tasks to a provider who offers IT network management solutions exclusively tailored for community banks.




 Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible.
Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible. 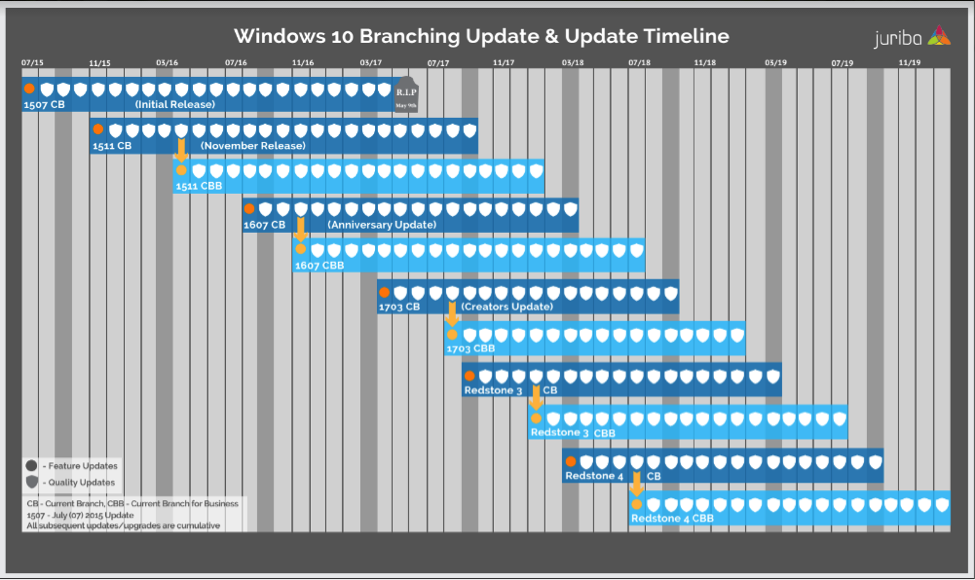




 Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank.
Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank. 





 This guidance is always changing, and financial institutions must adapt to regulatory demands. IT auditors and examiners will look for evidence of a thorough risk assessment; make sure that written policies and procedures align with the assessment; and then verify that controls and daily practices are appropriate.
This guidance is always changing, and financial institutions must adapt to regulatory demands. IT auditors and examiners will look for evidence of a thorough risk assessment; make sure that written policies and procedures align with the assessment; and then verify that controls and daily practices are appropriate.











 Oconee State Bank had already successfully implemented a previous version of Safe Systems’
Oconee State Bank had already successfully implemented a previous version of Safe Systems’ 
 Safe Systems currently monitors more than 20,000 devices and roughly 80% of all issues addressed come through our monitoring systems. Just by implementing Safe Systems NetComply One with SSAI, the number of alerts sent to an IT support team is decreased by an average of 89%. By effectively correcting known problems and only notifying your team about more significant issues, SSAI creates tremendous value for your institution, your employees and your infrastructure.
Safe Systems currently monitors more than 20,000 devices and roughly 80% of all issues addressed come through our monitoring systems. Just by implementing Safe Systems NetComply One with SSAI, the number of alerts sent to an IT support team is decreased by an average of 89%. By effectively correcting known problems and only notifying your team about more significant issues, SSAI creates tremendous value for your institution, your employees and your infrastructure.
 Regulations define cybersecurity as:
Regulations define cybersecurity as: Regulators expect financial institutions to be not just cyber-secure, but cyber resilient, and that requires close cooperation with all their critical third-parties. Assessing and managing risks, and developing capabilities for response and recovery in the event of disruptions regardless of where they may occur, requires financial institutions to have proven plans in place to meet regulatory expectations. The FFIEC has issued specific guidance on how it expects organizations to manage this process. The FFIEC IT Examination Handbook’s “
Regulators expect financial institutions to be not just cyber-secure, but cyber resilient, and that requires close cooperation with all their critical third-parties. Assessing and managing risks, and developing capabilities for response and recovery in the event of disruptions regardless of where they may occur, requires financial institutions to have proven plans in place to meet regulatory expectations. The FFIEC has issued specific guidance on how it expects organizations to manage this process. The FFIEC IT Examination Handbook’s “










 In today’s banking environment, community banks recognize and embrace the use of technology and remain committed to investing in new technologies and services moving forward. In fact, nearly 77% of respondents claim they are spending more on technology today than they have in the past. However, the challenge often lies in trying to keep pace with the rapid rate of change that is influencing their business. Community banks are continuing to explore ways to enhance and augment their IT departments, as many institutions struggle to maintain adequate personnel needed to manage the complex activities required of the IT department. To counter this, 71% of respondents have turned to outsourcing their network management and 63% have outsourced their IT support.
In today’s banking environment, community banks recognize and embrace the use of technology and remain committed to investing in new technologies and services moving forward. In fact, nearly 77% of respondents claim they are spending more on technology today than they have in the past. However, the challenge often lies in trying to keep pace with the rapid rate of change that is influencing their business. Community banks are continuing to explore ways to enhance and augment their IT departments, as many institutions struggle to maintain adequate personnel needed to manage the complex activities required of the IT department. To counter this, 71% of respondents have turned to outsourcing their network management and 63% have outsourced their IT support.

 Banks should make continual service improvement a key part of their overall corporate culture. These changes can be identified by a single resource or through a committee focusing on operational improvement. Allocating time and resources to focus on the right aspects of new technology and process improvement is key as even the smallest incremental changes can have the ability to provide a significant positive impact.
Banks should make continual service improvement a key part of their overall corporate culture. These changes can be identified by a single resource or through a committee focusing on operational improvement. Allocating time and resources to focus on the right aspects of new technology and process improvement is key as even the smallest incremental changes can have the ability to provide a significant positive impact. 

 It is important to make sure that all functional areas of the institution are involved in testing. This means that in addition to the Senior Management and Information Security roles defined in your plan, the team should also consist of key department heads with detailed operating knowledge of the processes and functions impacted by your scenario. These individuals must be aware of how to quickly recover and adequately support customer needs, regardless of whether normal operating procedures are available. Therefore, tests should cover the steps departmental managers must take to complete functions manually or in an alternate way. Although technology is important, the disaster response must not hinge on waiting for technology glitches to be resolved. Your departmental specialists know how to do their job under normal circumstances, but including them in testing allows them to gain familiarity with their alternate procedures in a specific emergency scenario.
It is important to make sure that all functional areas of the institution are involved in testing. This means that in addition to the Senior Management and Information Security roles defined in your plan, the team should also consist of key department heads with detailed operating knowledge of the processes and functions impacted by your scenario. These individuals must be aware of how to quickly recover and adequately support customer needs, regardless of whether normal operating procedures are available. Therefore, tests should cover the steps departmental managers must take to complete functions manually or in an alternate way. Although technology is important, the disaster response must not hinge on waiting for technology glitches to be resolved. Your departmental specialists know how to do their job under normal circumstances, but including them in testing allows them to gain familiarity with their alternate procedures in a specific emergency scenario.