Financial institutions need to stay on top of Microsoft Azure maintenance to efficiently use Microsoft cloud services and have effective controls across identity and access. Azure maintenance is also a matter of regulatory compliance.
Microsoft Azure maintenance encompasses Azure Active Directory, M365 (formerly called Office 365), Microsoft Exchange Online, and other associated Azure cloud services. Many institutions may not realize they are leveraging cloud solutions because it’s not always obvious where different technology services originate. Regardless of how an institution obtains Microsoft Exchange or M365, it creates a Microsoft tenant with Azure AD. Institutions are ultimately responsible for these tenants and this includes properly securing and maintaining them.
The Federal Financial Institutions Examination Council (FFIEC) expects institutions to engage in effective risk management for the “safe and sound” use of cloud computing services. The council indicated as much in its statement on “Security in a Cloud Computing Environment,” saying: “System vulnerabilities can arise due to the failure to properly configure security tools within cloud computing systems. Financial institutions can use their own tools, leverage those provided by cloud service providers, or use tools from industry organizations to securely configure systems, provision access, and log and monitor the financial institution’s systems and information assets residing in the cloud computing environment.”
In addition, financial institutions are obligated to oversee third-party service providers and make sure that they use proper security controls. “Management should be responsible for ensuring that such third parties use suitable information security controls when providing services to the institution,” the FFIEC IT Handbook’s Information Security booklet stated. “Management should verify that third-party service providers implement and maintain controls sufficient to appropriately mitigate risks.”
Azure Active Directory
Azure Active Directory (Azure AD, AAD) is the primary identity platform across all Azure services. There are some standard maintenance objectives that financial institutions should meet with Azure AD.
Some of the key types of identities to review within Azure AD are users, devices, and enterprise applications. User maintenance is an area many people are familiar with, and it involves ensuring the list of users matches expectations. IT administrators should be on the lookout for new accounts; they should look for users who should not be there and delete or disable them if appropriate. For example, users may need to be purged from the list after they complete off-boarding procedures.
With device maintenance, it is important to be aware of all the devices that the organization has placed into Azure AD. IT administrators should ensure that, at least for Windows OS devices, they follow the established naming convention. They should delete “stale” or inactive devices and ensure that all devices—whether desktop or mobile—adhere to established compliance policies.
The maintenance for enterprise applications—objects with some form of connectivity with your Azure tenant—involves making sure various service apps meet expectations for functionality. Administrators should review the apps’ properties to ensure the best controls are being applied. For instance, this could include addressing apps that have an expired certificate.
Other important maintenance areas within Azure AD include reviewing privilege role assignments to ensure their validity, scrutinizing delegated administration partners to confirm their level of access, and “right-sizing” the number and types of licenses to avoid being over or under-provisioned.
M365 and Exchange Administration
SharePoint Online, Exchange Online, and OneDrive are core components of M365 and as such, they require strategic maintenance. Here are some important areas IT admins should address to maintain these services:
- Usage reporting— Monitor usage reports to ensure they match the institution’s expectations. Anomalies in consumption and storage could indicate a possible security or compliance concern.
- Cleaning up files— Delete old, unused files from OneDrive or SharePoint. Administrators can solicit help from users by notifying those who are approaching their limits.
- File retention policy— Automatically delete files based on a set schedule or duration, such as anything older than seven years.
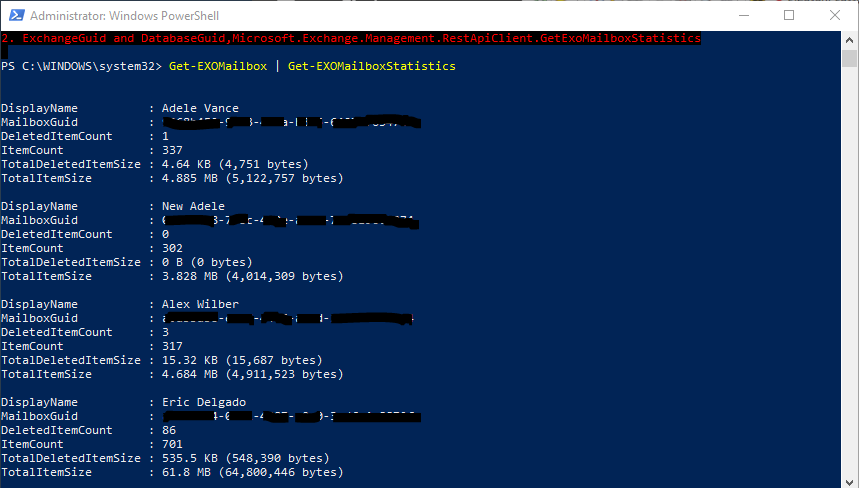
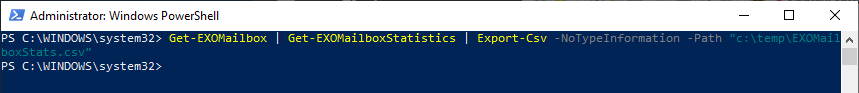
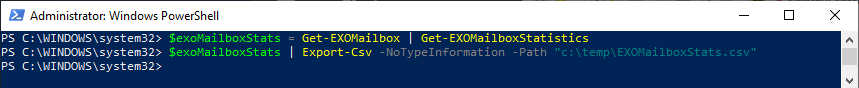
- Exchange Online mailbox usage— Notice mailbox statistics before users reach their limit to avoid service disruptions—and complaints.
- Distribution list review— Make sure distribution lists contain the appropriate members for the most effective targeting.
- Exchange Online mobile devices— Keep track of the details about users’ mobile devices to gain additional insights for achieving maintenance objectives and compliance.
For more information, listen to our “Azure Maintenance —The Basics Every IT Administrator Should Know” webinar.