The number of cyber-attacks directed at financial institutions of all sizes is continuing to grow and cybersecurity experts expect the trend toward increasingly sophisticated cyber-attacks to continue. Community banks and credit unions are prime targets for cyber criminals due to the sensitive data they house. As consumers and businesses continue to use electronic devices such as computers, tablets, and smartphones to perform financial transactions online, vulnerabilities continue to increase. A cyber breach can be devastating due to the costly ramifications, not to mention compromised customer confidence and reputational damage.
As a result of this heightened risk of cybersecurity attacks, regulators are heavily scrutinizing bank processes to verify that these institutions can effectively safeguard sensitive financial information. While not yet a requirement, the FFIEC’s Cybersecurity Assessment Tool (CAT) serves as the key guidance used to determine whether an institution is adequately prepared for a cybersecurity incident and in full compliance with federal regulations. In response, many banks and credit unions are now completing the assessment to assess their cybersecurity posture, determine their next steps to strengthen cybersecurity processes and better meet examiner expectations.
While completion of the assessment has proven itself beneficial, many financial institutions find the 100+ page assessment to be too cumbersome of a task to successfully manage and fully understand. As a result, they decide they need to find a more efficient way to complete the assessment, understand their level of risk and make improvements to their IT environment.
 This was the case for Pembroke, N.C.-based Lumbee Guaranty Bank. To ensure his institution maintained compliance, Austin Maynor, Information Security Officer at Lumbee Guaranty Bank, manually filled out the CAT with the help of a spreadsheet, but quickly found this process to be an extremely time-consuming project to complete. He determined the bank needed a solution that could give them a better understanding of where they were in terms of cybersecurity preparedness and where they needed to be in order to maintain compliance.
This was the case for Pembroke, N.C.-based Lumbee Guaranty Bank. To ensure his institution maintained compliance, Austin Maynor, Information Security Officer at Lumbee Guaranty Bank, manually filled out the CAT with the help of a spreadsheet, but quickly found this process to be an extremely time-consuming project to complete. He determined the bank needed a solution that could give them a better understanding of where they were in terms of cybersecurity preparedness and where they needed to be in order to maintain compliance.
Streamlined CAT Completion Solution
As a long-time customer of Safe Systems, the bank decided to implement the Cybersecurity RADAR™ solution, a cybersecurity product that combines compliance expertise with an Enhanced Cybersecurity Assessment Tool (ECAT) application. The solution allows staff to quickly generate reports, document notes and save examination results to review each year.
For Lumbee Guaranty Bank, Cybersecurity RADAR streamlined the process of filling out the CAT and helped the bank improve its cybersecurity processes. With the automated application, Lumbee Guaranty Bank significantly reduced the amount of time spent completing the CAT from days to less than 4 hours. In addition, Safe Systems’ evaluation of the bank’s responses helped clearly illustrate to the bank where they were in regards to compliance and baseline expectations.
“The Cybersecurity RADAR solution has been a great addition to our bank, helping us gain meaningful operational efficiencies while continuing to grow and strengthen our cybersecurity program. We are grateful to have a true partner like Safe Systems helping us navigate the latest compliance guidelines and effectively streamline our most important processes.”
For more information, download our cybersecurity case study, “Lumbee Guaranty Bank Streamlines Cybersecurity Processes.”






 Even though the CAT is voluntary, all financial institutions are required to evaluate inherent risk and cybersecurity maturity in some way, which requires a robust assessment program. Completing the CAT is a good way to prepare for audits since the guidelines provide community banks and credit unions with detailed information on the federal government’s expectations for cybersecurity preparedness. The CAT enables financial institutions to identify vulnerabilities, fill in security gaps, and demonstrate a stronger security posture before the examination begins.
Even though the CAT is voluntary, all financial institutions are required to evaluate inherent risk and cybersecurity maturity in some way, which requires a robust assessment program. Completing the CAT is a good way to prepare for audits since the guidelines provide community banks and credit unions with detailed information on the federal government’s expectations for cybersecurity preparedness. The CAT enables financial institutions to identify vulnerabilities, fill in security gaps, and demonstrate a stronger security posture before the examination begins. 

 One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.
One challenge financial institutions face is that running and maintaining server hardening services strains the resources of a limited IT staff. Banks and credit unions are already swamped with ensuring their servers are secure, which includes examining vulnerability assessment reports, fixing numerous findings, troubleshooting services, and addressing patch management, antivirus, and other activities on an ongoing basis.


 Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible.
Knowing key dates in a product’s lifecycle helps organizations make informed decisions about when to upgrade or make other changes to software. Microsoft ended support in May 2017 for build number 1507, which means it no longer provides automatic fixes, updates, or online technical assistance for this version. Without Microsoft support, financial institutions will no longer receive important security updates that can help protect PCs from harmful viruses, spyware, and other malicious software that can steal information and infect networks. Because of this, we recommend systems be upgraded before they reach their end of life whenever possible. 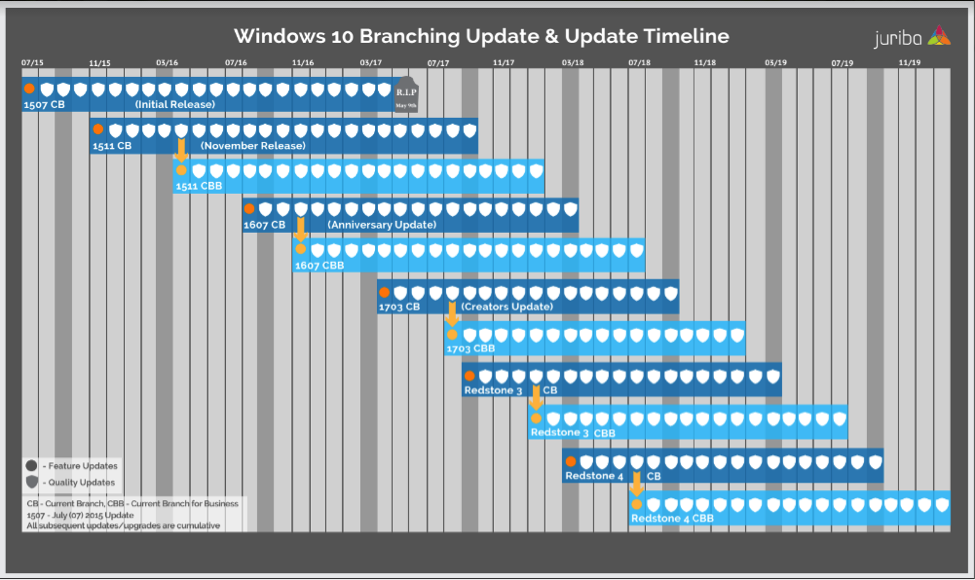







 Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations.
Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations. 



 Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank.
Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank. 



 To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.
To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.










