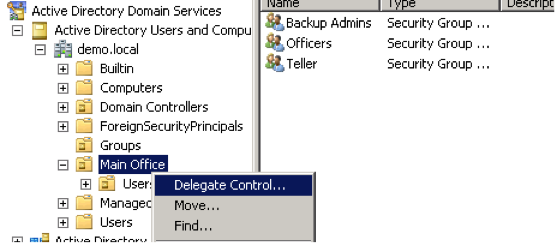
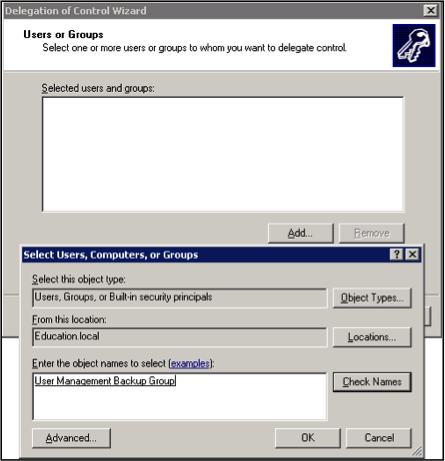
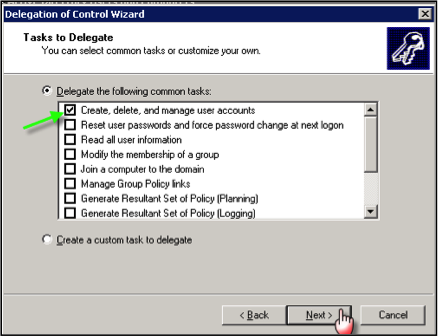
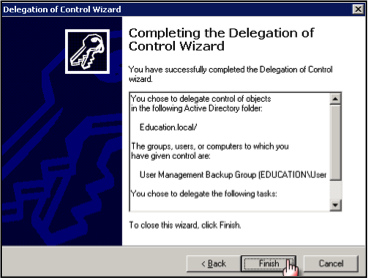
It is very common to have people that you know in the community who run great IT companies. Many of these people often have personal relationships with the bank and bank employees, may have accounts with the bank, and may even have stock or sit on the board of the bank. In addition to the established personal relationship, most banks also like the idea of having someone who can physically be at the bank to assist when something breaks or needs attention.
These are all valid reasons for using a local IT service provider; however, it is also important to understand the risks that these providers pose to your institution, especially given today’s oversight environment.
-
Examiner expectations
In recent years the FFIEC has published very clear regulations focused on vendor management. To this point, several IT Examination Handbook booklets address managed security providers and cloud services. For example, the Outsourcing Technology Services and Business Continuity Planning booklets both contain explicit guidance on technology service providers.
-
They don’t know the expectations specific to our industry
In the same addenda mentioned above, the regulators address risk assessment processes for IT vendors. They specifically mention knowing how many financial institution customers the vendors have versus their total customer counts. Vendors that don’t have a large number and percentage of their customers as financial institutions may not have the proper controls in place to validate compliance.
From a purely technical perspective, working with banks is more complex. For example, one of the great advantages of technology management today is the ability to work remotely. Vendors with remote access that have no way to log and track access are not acceptable from either a business or compliance risk perspective.
-
Limited knowledge of banking applications
One recurring theme with vendors that support multiple industries is that they are usually very good at supporting systems that are common among their customer base. This includes items like Microsoft Office, email, printing and network communications. When vendors are supporting your systems their knowledge of your banking applications is vital. Making sure that the teller, new account, imaging, loan, and other applications continue to work within the updated IT infrastructure is imperative. In today’s world customers expect minimal downtime, and having a vendor with limited expertise in your bank’s critical applications lengthens the time required for problem resolution. When you need help with IT support, you don’t have time for your vendor to learn how the applications work before they start resolving the problem.
-
Lack of documentation and reporting
Most IT vendors are quite good at working to fix a problem or setting up systems to work correctly. However, that technical configuration is just a piece of the puzzle. As a regulated financial institution, you can’t outsource responsibility, so having proper reporting and documentation is imperative. You must prove that the way your devices are configured and managed adhere to your Information Security policies. For instance, if you can’t install a patch because it will break the teller system, you have to document the reasons why the patch was not deployed. This type of reporting and validation needs to be available so the technology steering committee and senior management can make informed decisions about IT issues.
IT vendors that provide services, including antivirus, patch management, and event logging, have heightened expectations from the regulators. Your institution must perform a risk assessment on each vendor to validate that they conduct themselves in a sound and secure manner. Ideally, technology service providers should submit themselves to independent audits that take Trust Service principles into account (security, availability, processing integrity, confidentiality and privacy), and provide evidence in the form of an audit report. Many local IT support companies may not have the audits to validate that they are managing outsourced business processes consistent with the way financial institutions must manage them.
Perhaps more importantly, auditors and examiners will also expect a thorough paper trail to prove that daily practices match defined policies and procedures. In today’s ever-changing environment of regulatory compliance requirements, it is essential your financial institution’s policies, procedures and practices are in perfect alignment with regulator’s expectations. Not doing so can cost your bank severely.
As a reputable partner to community banks, Safe Systems specializes in delivering technology, security and compliance products and services. We understand that community financial institutions like yours are under pressure to manage the constant evolution of technology and compliance. We maintain the proper audit certifications (SOC 2, Type II) to assure your examiners that our business practices are sound and secure. With our expert solutions, you can stay ahead of this ever changing environment while managing costs and limited resources.

Dispelling 5 IT Outsourcing Myths within Financial Institutions
Learn why five of the most commonly believed “facts” about IT outsourcing within community financial institutions are actually myths.