How to Delegate Control in Active Directory Users and Computers
The Least Privilege Dilemma
A common trend from Auditors and Examiners lately is the review and questioning of accounts with administrative-level access. A linchpin for information security, The Principle of Least Privilege, states that an individual or account should only be granted the minimum amount of access needed to accomplish the role defined for them. Managing user accounts in Microsoft’s Active Directory is one place where this principle can be overlooked. The “easiest” way to allow someone access to manage users (unlock, reset password, create, delete, etc) is to add them to the Domain Admins security group. It is a rather common practice for institutions to grant an individual a second network login with these administrative privileges in order for that individual to service day-to-day user account needs in Active Directory Users and Computers (ADUC).
While this approach is appropriate in some cases, a security issue arises when the individual’s sole administrative responsibility is managing users. Granting a user Domain Administrator access, enables them to do much more than managing users. Domain Admins can remotely access servers, change permissions on folders, create/edit group policy, view contents of folders, and much more. While you may trust the user not to abuse their access, it can be difficult to defend this high level access during an audit.
Why Delegate Control?
If you have individuals who need “administrative access” strictly for resetting or unlocking a password, then you should consider delegating control. You can delegate control to a user for account administration without giving them the extraneous and potentially dangerous access a traditional administrative account commands. Typically, giving a user this reduced degree of access is more than sufficient for the job they need to perform. This can be done at a Domain level or, depending on your ADUC structure, more granularly at the Branch level.
The next few sections offer different scenarios of how you may choose to implement this.
Step-by-Step Instructions
I’ve detailed 3 different options below for delegating varying levels of user management in the steps below, ordered from the option with the greatest amount of control to the option with the least. Please choose the option that best fits your institution’s needs. All 3 option start with the same “Prep Work,” where you will create a group and decide where to delegate control.
A recommendation before you begin: While reporting on which users have Domain Admin group membership is easy, reporting on which users have certain delegated controls is not easy at all. For this reason, I recommend creating groups in ADUC and applying all delegated controls to these groups rather than to individual user accounts. Not only will this will grant you more flexibility to add users to (or remove users from) this group as business needs change, but the group will also act as a reporting touchpoint. Whether you take advantage of Safe Systems monthly reports posted to TheSafe, or if you use a tool like Dumpsec to monitor ADUC Users and Groups, tracking a single group is much easier than keeping tabs on multiple delegated employee accounts.
Prep Work (All Options)
- Create a group as mentioned above to which you can apply these rights.
Again, you can assign these rights to individuals instead of groups, but reporting and managing this going forward becomes an issue.
In Active Directory, right-click the Organizational Unit (folder icon with pc image on it) in which you wish to create the new group, and choose the option to create a new group object. Name the group, choose the scope, and select “Security” for the Group Type.
- Right click where you want these rights applied. There are two options I will list here – Domain-level or Organizational Unit-level.
First, the Domain-level. Right click on the Domain and delegate control, giving the group the ability to make these changes to everyone in the domain.
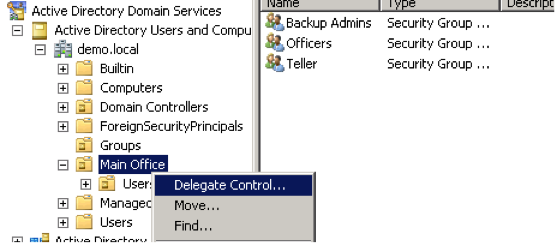 Or, right click on a specific Organizational Unit, and delegate the control at that level. This will limit the controls assigned to only the accounts under the Organization Unit. This is a good option if you want a specific user at a branch to only manage the users at their branch.
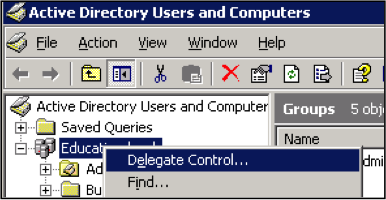
Or, right click on a specific Organizational Unit, and delegate the control at that level. This will limit the controls assigned to only the accounts under the Organization Unit. This is a good option if you want a specific user at a branch to only manage the users at their branch. - Assign the group or individual to get these delegated controls, then click OK to close the Select Users, Computers, or Groups window. Click Next to continue.
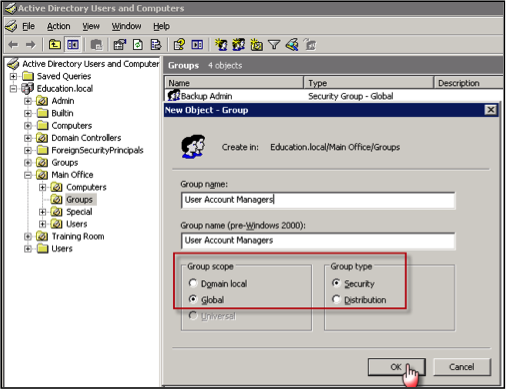
OPTION 1: Delegating the ability to Add/Remove/Reset/Unlock Users
-
Consider creating a separate account for the user to assign these enhanced security rights. For example, their login account for logging into the network and performing their daily task may be JDoe, but a separate account named John.Doe may be created and added to the security group that receives this delegated control.
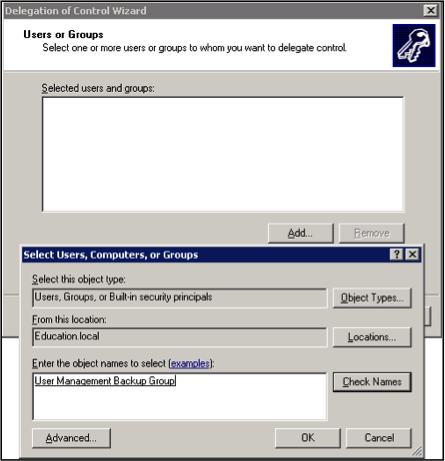
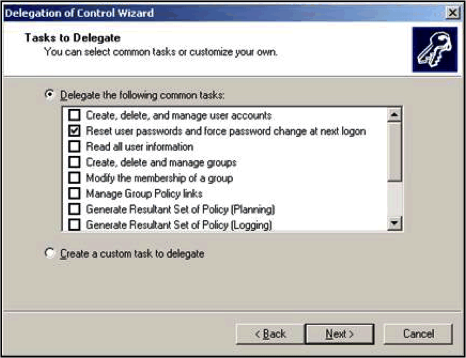
- Select the specific rights you wish to delegate, then click Next. For this option, you will choose the option to “Create, delete, and manage user accounts”.
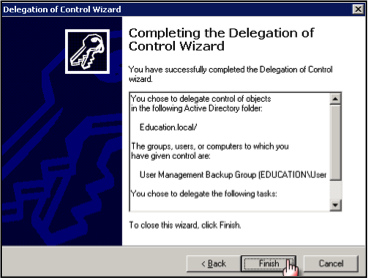
- Click Finish and you are done.
OPTION 2: Delegating the ability to Reset/Unlock Users
-
Less control than Option 1
- Follow all steps 1 – 3 in the Prep Work section above until you reach the Delegation of Control Wizard window.
- Assign the rights you want to delegate, then click Next. For this option you will need to choose the option to “Rest user passwords and force password change at next logon” to grant a more limited privilege level.
- Select Finish to complete.
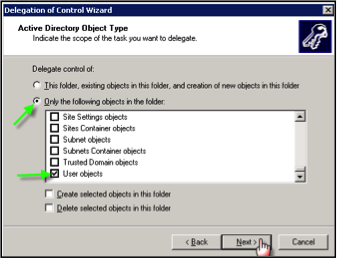
OPTION 3: Delegating the ability to Unlock Users only
-
Less control than Options 1 or 2
- Follow all steps 1 – 3 in the Prep Work section above until you reach the Delegation of Control Wizard window.
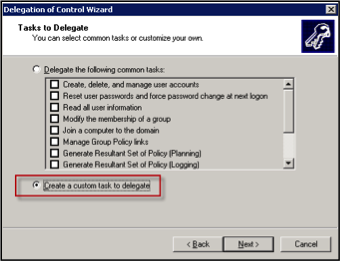
- There is no canned option for this limited degree of access, so you must create a custom task by selecting the “Create a custom task to delegate” radio button, then click Next.
- Select “Only the following objects in the folder” and then select “User objects”, then click Next.
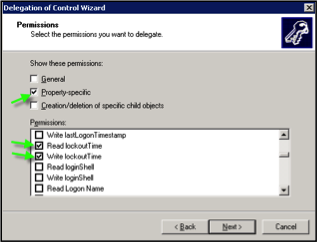
- Select “Property-specific” and then scroll down to find Read and Write Lockout times. Select these items as well, then click Next.
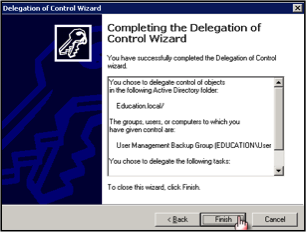
- Select Finish to complete.
Delegating controls is a great first step in implementing the Principle of Least Privilege on your domain level accounts. There is one aspect of this change that is not addressed in this article, and that is how the user will access ADUC after making this change. Please see our article in this month’s newsletter about Remote Server Administration Tools, as this will most likely be your best option to allow the users to manage ADUC going forward.

Dispelling 5 IT Outsourcing Myths within Financial Institutions
Learn why five of the most commonly believed “facts” about IT outsourcing within community financial institutions are actually myths.