Top 4 Security Solutions for a Layered Approach to Cyber Incident Response
When an incident occurs, it is critical for financial institutions to have proper logging tools in place to contain and control the incident and provide evidence to key external stakeholders such as law enforcement, third-party forensics teams, cyber insurance companies, etc. However, not all financial institutions have an advanced centralized logging system to perform perfect, historical investigations to understand malicious activity on their networks.
Ideally, community banks and credit unions embrace the fundamentals of a layered approach to security and understand the capabilities and tools that they already have at their disposal that can prove useful and actionable.
In this blog post, we’ll discuss some of the most common questions our customers have when investigating threats and the key tools we reach for that provide the evidence and conclusive answers to those questions.
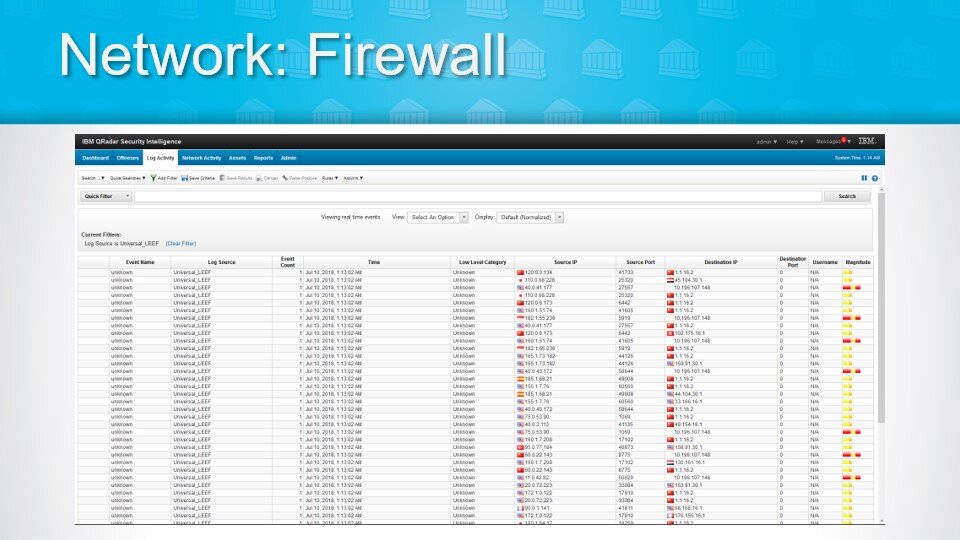
1. Network Firewall
We often reach for this tool when a financial institution is working to determine if one of their employees may have received a phishing email or clicked a malicious link. They want to know: who got the email; which user was an entry point for a piece of malware; or when did they connect to it? Relying on the memory of the user often doesn’t provide the detailed information needed to take action and find the true source of the problem. Logs, however, offer deeper insights. If we know the specific workstation or outside IP address, we can then look it up and decipher the entire transaction.
Firewalls, by their nature of design, generate a significant number of logs. The downside is that the sheer volume of logged content is very high and it’s difficult for any human to monitor and manage this amount of data effectively on their own without automated tools. Many community financial institutions are outsourcing firewall management to third-party providers that have created logging infrastructure just for the firewall to store the logs and make the data searchable and readable.
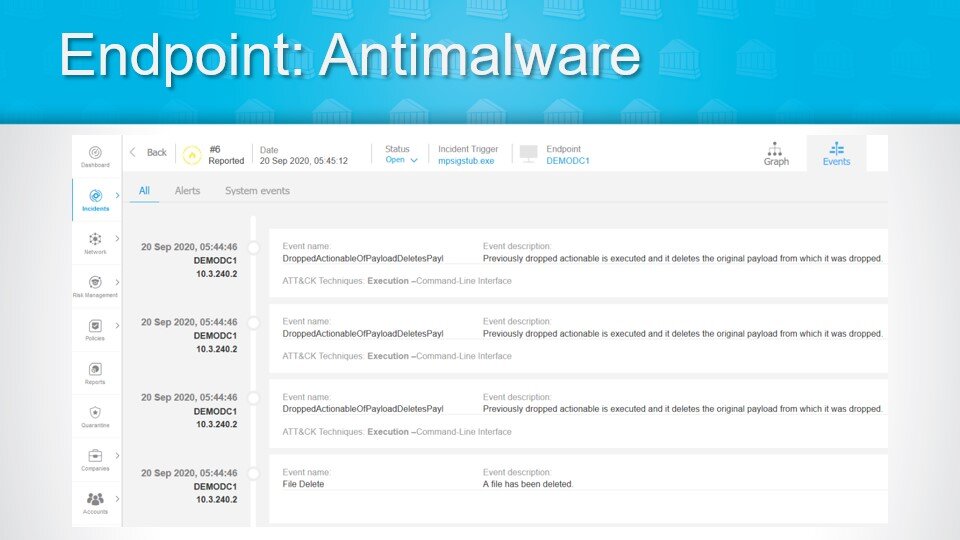
2. Endpoint: Antimalware
Antimalware and antivirus agent tools help financial institutions track down the precise point from which malware and viruses originated. Some of these have better logging capabilities than others, but many of them feature impressive investigative tools. We often reference this tool when a customer says: “I think someone might have opened an attachment they weren’t supposed to,” or “I think we might have some sort of infection that might be spreading, can you check it out for us?” With our antimalware tools, we’re able to track down exactly where it originated; who clicked what; and identify the actual origin point. The tool also enables us to break up the data and show a graphical representation of events.
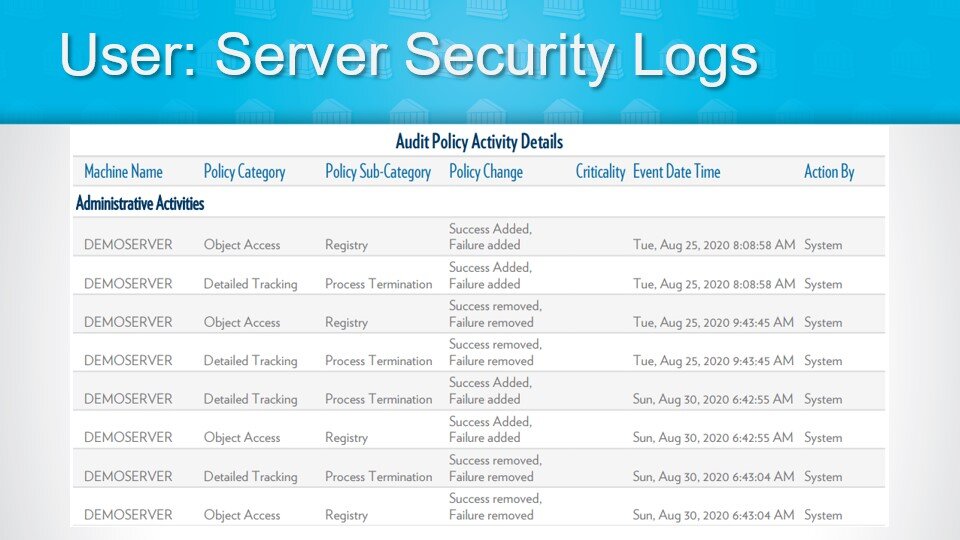
3. Server Security Event Logs
Security event logs record user logins and network access. We reach for these tools when we get questions from customers wanting to know which user logged into a certain application or who may have access to information that they shouldn’t. One of the most important areas to monitor are administrative logging events. If a bad actor gets into your network and gains access to your active directory, they then have the proverbial “keys to the kingdom” with the ability to create accounts, or even worse, admin accounts. However, the one thing they can’t hide is all of the activity they’ve done on the network as long as you’re monitoring these logs.
IT personnel are required to have some mastery of security event logs on the servers and especially on domain controllers to meet examiner expectations, but it requires expertise and research to understand which events are important. For example, with each new version of Windows comes a new set of alerts and often, alerts that were important in a previous version get replaced by something new. This is very challenging to manage along with other important IT activities. Working with a third-party provider can help you stay on top of the latest Windows updates and emerging threats with alerts and reports to proactively monitor the network and effectively thwart attacks.
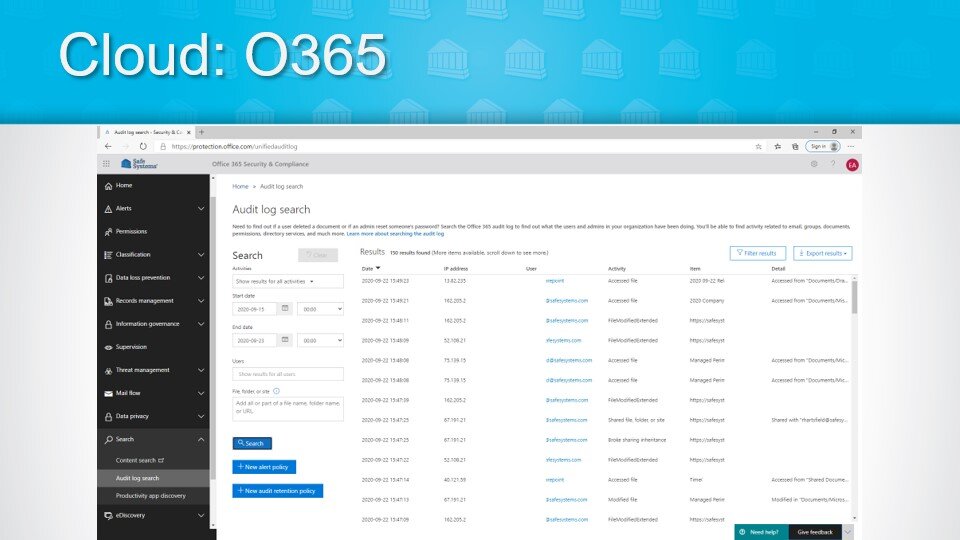
4. Cloud – O365
Most financial institutions use Microsoft O365, but they may not be taking full advantage of all the capabilities it has to offer as there is a host of fantastic logging and audit capabilities that are not turned on by default. So, if you’re an O365 subscriber, you need to review all security settings and make sure you have them turned on.
At Safe Systems, we do this when we onboard customers to our managed O365 offering to protect against e-mail-borne threats. A few key items we make sure our customers are monitoring include:
- Email Forwarding – IT admins should make sure that user mailboxes don’t have forwarders set up that point to any other mailbox, especially not an external email address. Without multi-factor authentication turned on, bad actors can access your mailbox; set up forwarding; and monitor correspondence between you and a customer undetected.
- Delegated Permissions – IT admins should also check delegated permissions to look for unauthorized access to employee mailboxes. Bad actors often use this tactic to spy on email communications between financial institution staff and customers.
We encourage all financial institutions to implement these four tools for cyber incident response and make sure you understand how to collect important logging information to have conclusive evidence right when you need it.
For more information, watch our recorded webinar, “Not If, But When: Best Practices for Cyber Incident Response.”

