What the NCUA’s 2020 Supervisory Priorities Mean for Your Credit Union’s ACET Cybersecurity Efforts

The National Credit Union Association (NCUA) released the Automated Cybersecurity Examination Tool (ACET) in 2017 to help credit unions assess their current cybersecurity preparedness level and since then, examiners have been primarily focused on making sure the assessment is completed. However, in January, the NCUA issued its supervisory priorities stating, “In addition to the ACET, the NCUA will be piloting new procedures in 2020 to evaluate critical security controls during examinations between maturity assessments.” This means that credit unions must now go beyond simply completing the ACET to successfully meet these expectations.
Safe Systems compliance expert, Tom Hinkel, held a webinar last month covering the difficulties of filling out the ACET and how credit unions can best prepare for the NCUA’s new procedures. Key points from the webinar included:
Challenges in Accurately Completely The ACET
Before taking the next steps in the ACET process, it is important for credit unions to understand how misinterpreting a question or a declarative statement can significantly impact the accuracy of the overall assessment. If the responses are inaccurate, then the conclusions aren’t going to be correct either. The main challenge is that most of the items in the inherent risk profile are open to interpretation, and how a credit union chooses to interpret those questions affects where it will set its risk level for each part of the assessment. The NCUA has added pop-up descriptions throughout the assessment to help with interpretation and while this is useful, it does not eliminate all possibility of misinterpretation. Having access to compliance expertise during this process can help provide more clarity for credit unions to ensure that each answer is truly accurate.
Steps Toward Cyber Maturity
Originally defined by the FFIEC, the five steps of the cybersecurity assessment process include: 1) completing the ACET; 2) identifying gaps; 3) determining desired state of maturity; 4) developing an action plan; and 5) reporting and reevaluating. However, many credit unions cycle back and forth between step one and step five without making sure that steps 2, 3, and 4 are completed as well. Without looking at the output of the assessment and making adjustments based on the results, the institution hasn’t improved its cybersecurity posture. It has just defined it. With the NCUA’s new supervisory priorities, examiners now expect credit unions to take the appropriate next steps to continually evolve their cyber maturity based on risk.
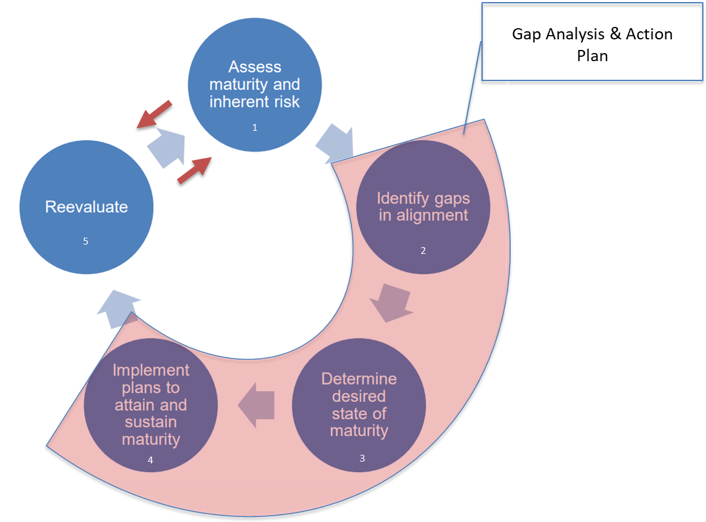
Gap Analysis
The webinar covered how credit unions can better analyze their risk and control levels and identify cybersecurity gaps. A “gap” is defined as the difference between an institution’s residual risk level (risk after applying controls) and its risk appetite (where management expects the credit union to be). However, the ACET is clear that the risk assessment portion is designed to capture inherent risk, and the credit union must then be able to get from inherent risk (before controls are applied) to residual risk in order to conduct a meaningful analysis of its risk and control areas. The ACET doesn’t provide a straightforward way to do this, unfortunately, but it is a requirement in order to accurately identify the institution’s gaps.
Desired State of Maturity
Once an institution identifies “where it is”, the next step is to determine its “desired state of maturity,” defined as any level at (or below) the institution’s risk appetite. Cyber risk appetite—in turn—is defined as the amount of risk the institution is willing to accept when trying to achieve its objectives. The risk appetite is set and approved by the Board, and while they may decide a single enterprise-wide cyber risk appetite is sufficient, generally they will prefer to assign a separate risk appetite to each business process. Apart from how your institution decides to define cyber risk appetite, it is a critical step to get to the action plan.
Action Plan
The action plan is made up of the declarative statements that the institution plans to achieve prior to the next assessment in order to close the gap between the “current level” and the “desired state.” Because the threat environment is continually increasing, examiners now expect to see steady incremental increases and improvement over time. Essentially, if an institution is deemed stable on the risk side and doesn’t increase on the control maturity side, their cybersecurity posture is effectively moving backward. The webinar highlights how credit unions can use their ACET results to drill down from the domain level to the contributing components and from there to the individual declarative statements to identify and prioritize specific action plan objectives.
Report and Reevaluate
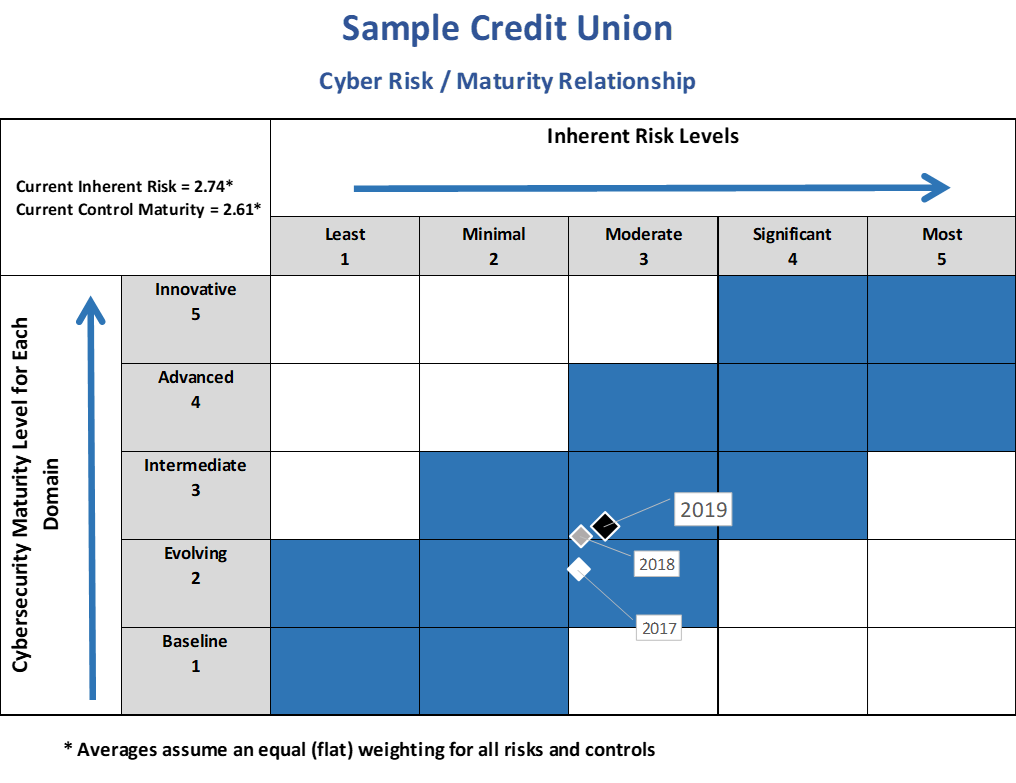
Finally, a significant part of the assessment is not just understanding where you are, where you need to be, and how you’re getting there, but also communicating your efforts clearly to all stakeholders. Credit unions need to show what improvements have been made and how those results were achieved. The FFIEC provided a document to CEOs and Boards to assist with this process. We believe superimposing your results on this graph demonstrates an effective way to present cybersecurity posture to your auditors and examiners, as well as the IT steering committee, and the Board:
If you’d like to find out some best practices and tips to help improve your cybersecurity process and increase your compliance posture, download our recorded webinar: “Cybersecurity Preparedness: You’ve Completed the ACET, but Is That Enough? What Do Regulators Expect Next?”



