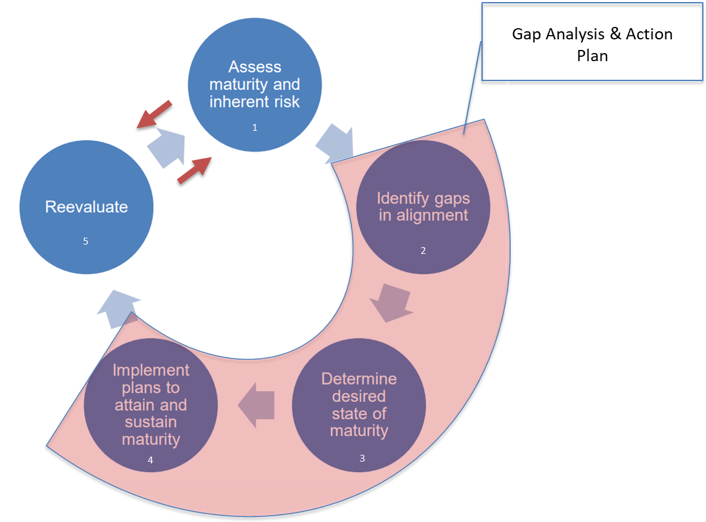
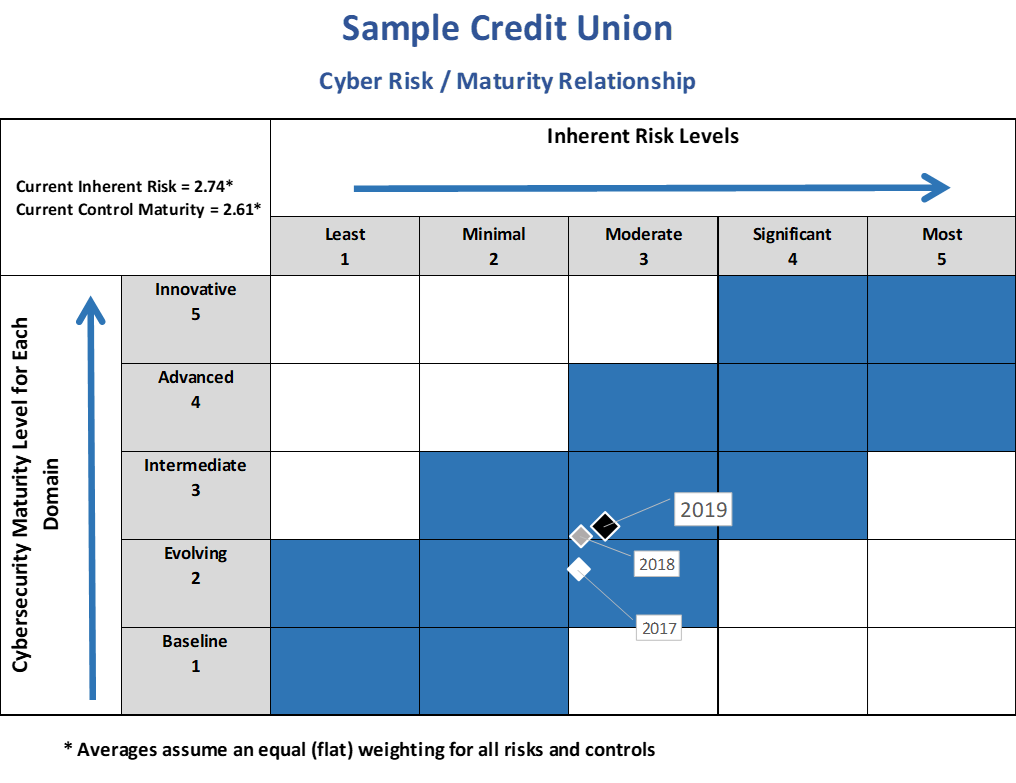
We recently conducted a sentiment survey to ask our community bank and credit union customers about their top worries for 2020. Cybersecurity was at the top of the list for most institutions and not without reason. According to a recent Boston Consulting Group report, cyber-attacks are 300 times more likely to hit financial firms than any other company.
In an effort to help community bank and credit union CEOs prepare for cybersecurity threats in 2020, I recently shared a video from my “Banking Bits and Bytes Super Duper CEO Series,” covering the current threat landscape and what financial institution CEOs need to look out for over the next 12 months. Here are three key areas to focus on:
Business Email Compromise
Business email compromise isn’t a new cybersecurity threat to financial institutions, but we’ve recently seen increased incidents of these malicious emails in community banks and credit unions. We often see this happen when the CFO at a bank receives an email that appears to come from the CEO asking them to send a wire transfer on their behalf. These types of emails are able to easily slip through email filters because they don’t contain any malicious code. It is just a plain text message so it can easily be viewed as a non-threatening email to an employee. This is why user security awareness training is the most important counter measure to prevent employees from interacting with these messages.
Extortion Emails
We’ve also seen a rise in extortion emails claiming to have compromising information about a financial institution executive that will be released to the public unless a ransom is paid. In these emails, hackers may also claim to know username and password pairings and say they have hacked into a victim’s computer. Fortunately, these threats are rarely – if ever — true or accurate, but this has still raised concerns from many executives.
The best way to guard against this sort of attack is to use different passwords for different accounts and to change those passwords often. Multi-factor authentication is another very effective tool in protecting against extortion. Also, ensuring your institution has quality user security awareness training prevents someone from mistakenly responding to these emails.
Internet of Things (IoT)
Most people think of the IoT as devices like the Amazon Echo or the Google Nest Thermostat, but that’s not what we’re talking about here. While most Windows PCs in financial institutions have effective security measures in place to protect against threats, there are other items on the network like multi-function printers; network connected LaserJet printers; the digital signage in front of the institution; or the even the DVR system or security camera from third-party providers, that can present an opportunity for criminals.
These devices are often on the network and as a result, can “see” the other devices connected to the network. They are often communicating with devices outside of the institution and unfortunately, you don’t have the ability to control the software that runs these devices; manage the patch level; or dictate who the device can talk to or how it does so. Financial institutions can compensate for this lack of control through careful network topology design; careful perimeter security rules; and installing detective technologies on the network to know when these IoT devices are up to no good.
As cybersecurity threats become more complex, so too must the measures that CEOs employ within their institutions to counter these threats. To learn more about security threats and how to protect your institution, watch the full “Banking Bits and Bytes Super Duper CEO Series” below.