As financial institutions increasingly rely on outsourced providers, third-party management is becoming a more critical aspect of managing risk. Institutions depend on third-party providers for a variety of essential services, including technology, operations, and marketing. And while these entities offer significant benefits, such as cost savings and improved efficiency, they also pose a substantial risk. We often refer to this as “inherited” risk, as institutions will inherit the residual risk of the third party. If not properly identified, measured, and addressed, inherited risk can expose financial institutions to threats such as regulatory non-compliance, operational downtime, and reputational damage. However, institutions can successfully mitigate many of these risks by ensuring that they thoroughly vet outside providers prior to engagement, properly structure contracts, and employ ongoing monitoring and reporting.
Key Elements
The Federal Financial Institutions Examination Council (FFIEC) has issued guidelines for managing vendor relationships effectively. These standards emphasize the importance of several key elements, including:
- Due diligence: Financial institutions must evaluate vendors’ financial stability, reputation, and regulatory compliance prior to engagement. This includes assessing vendors’ security controls, data protection policies, and disaster recovery plans.
- Contract management: Vendor agreements should clearly outline the scope of work, deliverables, and performance metrics. They should also include provisions for termination, dispute resolution, data disposal, and indemnification.
- Ongoing monitoring: Financial institutions must regularly monitor their third parties to ensure that they continue to meet contractual obligations and regulatory requirements. This includes periodic risk assessments, reviewing vendor reports, and could even include conducting on-site visits.
- Risk assessment: Institutions should assess the level of risk associated with each vendor relationship based on the services provided, the vendor’s access to sensitive data, and the potential impact of vendor failure. Doing so can help financial institutions allocate resources more effectively to minimize potential risks.
- Board and management oversight: Third-party management should be an ongoing topic of discussion at the board and management levels. This includes not only approving policies and procedures, but also reviewing risk assessments and monitoring reports, and making decisions about initiatives that require new vendor relationships.
Common Misconception
Risk management requires first identifying the risk’s source before it can be measured and mitigated. To accomplish this, it’s important to separate the risks of the underlying initiative from the risks of the third party that supports the initiative. With the possible exception of reputation risk, most of the risks surrounding the evaluation and implementation of a new initiative are associated with the initiative itself, not the third party. Simply put, if the strategic, operational, and regulatory risks would be present in the initiative regardless of the third party selected, it does not belong to the third party, it belongs to the initiative or project. We’ve found this to be a fairly common misconception, even among auditors and examiners.
Effective Solutions
Once the risk source is confirmed as associated with the third party as opposed to the initiative, institutions must create a protocol for what risks to assess and how to assess them (the inherent risk), what specific controls to implement, and the effectiveness of those controls assuming they will be correctly implemented and operate effectively (the residual risk). This is where an app can significantly help standardize and streamline the process. An automated third-party risk management program will identify and assign specific controls according to the specific risks and risk levels identified.
With the increased focus on third-party risk management, more banks and credit unions are finding that auditors and examiners expect institutions to not just identify appropriate controls, but to actually request, receive, and review them. Particularly key control documents, such as contracts, financials, and audit reports, such as System and Organization Controls (SOC) reports. However, knowing what to look for (and where to look) in these documents can be challenging. Partnering with a third-party service to assist you can provide a second set of eyes and additional expertise to ensure that these documents are supplying the necessary controls.
Other key features to look for in an effective third-party risk management program include the ability to assign one or more vendor managers, email reminders when tasks are due or overdue, automatic Office of Foreign Assets Control (OFAC) checks, the ability to easily identify and track complementary user entity controls (CUECs), the ability to store key vendor documentation and notes. Also, a robust on-demand reporting feature is important to be able to provide stakeholders with timely, accurate updates on the status of your third-party risk management program.
By associating with the right partner, financial institutions can develop a strong third-party risk management program that aligns with guidance, keeps data private and secure, and minimizes the impact of third-party cyber threats. Safe Systems, for example, offers a wide range of vendor management solutions to help institutions ensure regulatory compliance.














































 Be sure that all products your vendors are “sun setting” are budgeted to be updated or replaced. Also, ensure that key applications and settings are updated to the latest best practices, including:
Be sure that all products your vendors are “sun setting” are budgeted to be updated or replaced. Also, ensure that key applications and settings are updated to the latest best practices, including:



 Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations.
Conducting thorough due diligence includes demonstrating a strong understanding of a third party’s organization, business model, financial health, and program risks. To ensure the proper risk controls are in place, credit unions must understand a prospective vendor’s responsibilities and all of the processes involved. Examiners should evaluate if the credit union’s due diligence process includes background checks, examining the third-party’s business model, the determination of how cash flows move between all parties in the proposed third party arrangement, financial and operational controls, contract evaluation and accounting considerations. 



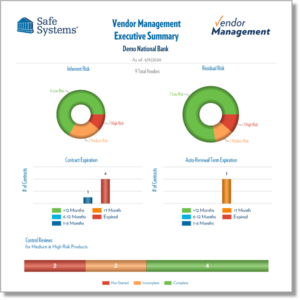
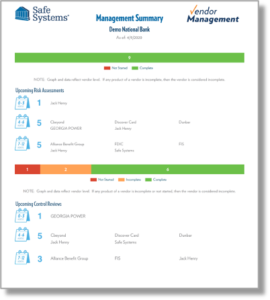
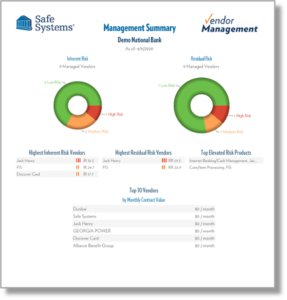
 Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank.
Furthermore, the bank is now able to centralize all documents in one location where staff and management can easily access them to provide detailed information for audit purposes and executive summaries for board review. Through this level of intelligent automation, paired with Safe Systems’ compliance support, the bank has significantly reduced the amount of time spent on vendor management processes, which has freed up resources to focus on additional revenue-generating activities for the bank. 



 To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.
To properly assess risk exposure for vendors/services, establish consistent criteria to appropriately weigh the risk each poses to the credit union. This will help you grade or designate a level of criticality and risk for each service and each vendor. For example, will a vendor have access to private member data? Will it operate with our core system? The criticality will have a significant impact on the review process, as a more critical service or vendor will ultimately require more due diligence to be performed.